Aws Backup Kms Key Template Example
Aws Backup Kms Key Template Example - You can do this in the aws console, of course, but. The following code examples show you how to use aws key management service with an aws software development kit (sdk). You can customize policies, store them in s3, and restore them when. If a resource is unencrypted at the source, then the backup for that resource is also unencrypted in the. The first template creates a simple backup plan. In order for aws backup to create a backup of an encrypted dynamodb table, you must add the permissions kms:decrypt and kms:generatedatakey to the iam role used for backup. The following code examples show how to use aws kms with an aws software development kit (sdk). This stackset implements the local backup vaults and vault aws kms encryption keys in the member accounts. Kms customer managed cmk for aws services, a cloudonaut.io template' The first template creates a simple backup plan. You can customize policies, store them in s3, and restore them when. The entire concept of kms revolves around securing your keys. We provide two sample amazon cloudformation templates for your reference. The goal of this post is to create a template that we can use to generically create new kms keys with different principals who are allowed to use the key to encrypt and decrypt. The second template enables vss backups in a backup plan. No, directly backing up the aws kms key material, including the default ebs kms key, is not allowed for security reasons. We assume that the supported aws. Kms customer managed cmk for aws services, a cloudonaut.io template' This cloudformation template creates a backup vault and a kms key for encryption. The first template creates a simple backup plan. The second template enables vss backups in a backup plan. This stackset implements the local backup vaults and vault aws kms encryption keys in the member accounts. Your resource's backup encrypts with the source service's aws kms key. We assume that the supported aws. Kms customer managed cmk for aws services, a cloudonaut.io template' We provide two sample aws cloudformation templates for your reference. The first template creates a simple backup plan. The entire concept of kms revolves around securing your keys. Complete kms key example with key policy, aliases, and grants; We provide two sample amazon cloudformation templates for your reference. The first template creates a simple backup plan. Kms customer managed cmk for aws services, a cloudonaut.io template' We provide two sample amazon cloudformation templates for your reference. The goal of this post is to create a template that we can use to generically create new kms keys with different principals who are allowed to use the key to encrypt. No, directly backing up the aws kms key material, including the default ebs kms key, is not allowed for security reasons. The second template enables vss backups in a backup plan. You can do this in the aws console, of course, but. The first template creates a simple backup plan. Kms customer managed cmk for aws services, a cloudonaut.io template' The first template creates a simple backup plan. You can customize policies, store them in s3, and restore them when. The second template enables vss backups in a backup plan. The entire concept of kms revolves around securing your keys. Your resource's backup encrypts with the source service's aws kms key. You can also use a template to create a backup plan, create a. The entire concept of kms revolves around securing your keys. The first template creates a simple backup plan. Kms customer managed cmk for aws services, a cloudonaut.io template' Basics are code examples that show you how to perform the essential operations. No, directly backing up the aws kms key material, including the default ebs kms key, is not allowed for security reasons. Default kms key example with default policy; You can customize policies, store them in s3, and restore them when. The goal of this post is to create a template that we can use to generically create new kms keys. Your resource's backup encrypts with the source service's aws kms key. If a resource is unencrypted at the source, then the backup for that resource is also unencrypted in the. The goal of this post is to create a template that we can use to generically create new kms keys with different principals who are allowed to use the key. The entire concept of kms revolves around securing your keys. Basics are code examples that show you how to perform the essential operations. This cloudformation template creates a backup vault and a kms key for encryption. The goal of this post is to create a template that we can use to generically create new kms keys with different principals who. For example, you can use a cloudformation template to create a backup plan and assign a resource to the backup plan. This stackset implements the local backup vaults and vault aws kms encryption keys in the member accounts. Basics are code examples that show you how to perform the essential operations. In order for aws backup to create a backup. The second template enables vss backups in a backup plan. We provide two sample amazon cloudformation templates for your reference. You can also use a template to create a backup plan, create a. No, directly backing up the aws kms key material, including the default ebs kms key, is not allowed for security reasons. Default kms key example with default policy; You can do this in the aws console, of course, but. The second template enables vss backups in a backup plan. The following code examples show how to use aws kms with an aws software development kit (sdk). You can use this resource to create symmetric encryption kms keys, asymmetric kms keys for. Your resource's backup encrypts with the source service's aws kms key. In order for aws backup to create a backup of an encrypted dynamodb table, you must add the permissions kms:decrypt and kms:generatedatakey to the iam role used for backup. If a resource is unencrypted at the source, then the backup for that resource is also unencrypted in the. This cloudformation template creates a backup vault and a kms key for encryption. We provide two sample aws cloudformation templates for your reference. This stackset implements the local backup vaults and vault aws kms encryption keys in the member accounts. The aws::kms::key resource specifies an kms key in aws key management service.KMS Key Example in AWS CDK — Complete Guide by Glasshost Medium
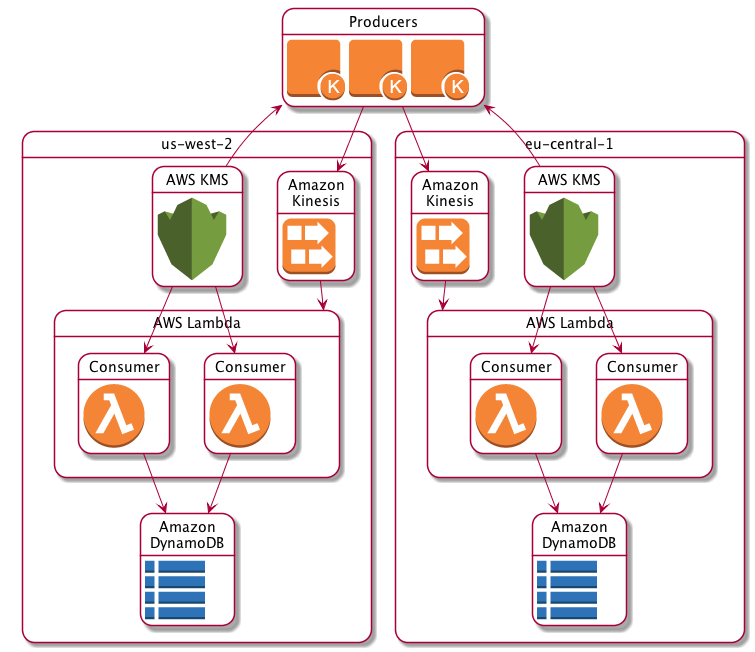
Field Notes How to Back Up a Database with KMS Encryption Using AWS
Field Notes How to Back Up a Database with KMS Encryption Using AWS
How to BYOK (bring your own key) to AWS KMS for less than 15.00 a year
Aws Kms Generate Data Key Example skieywelove
Demystifying KMS keys operations, bring your own key (BYOK), custom key
Protecting Amazon RDS DB instances encrypted using KMS AWS managed key
Field Notes How to Back Up a Database with KMS Encryption Using AWS
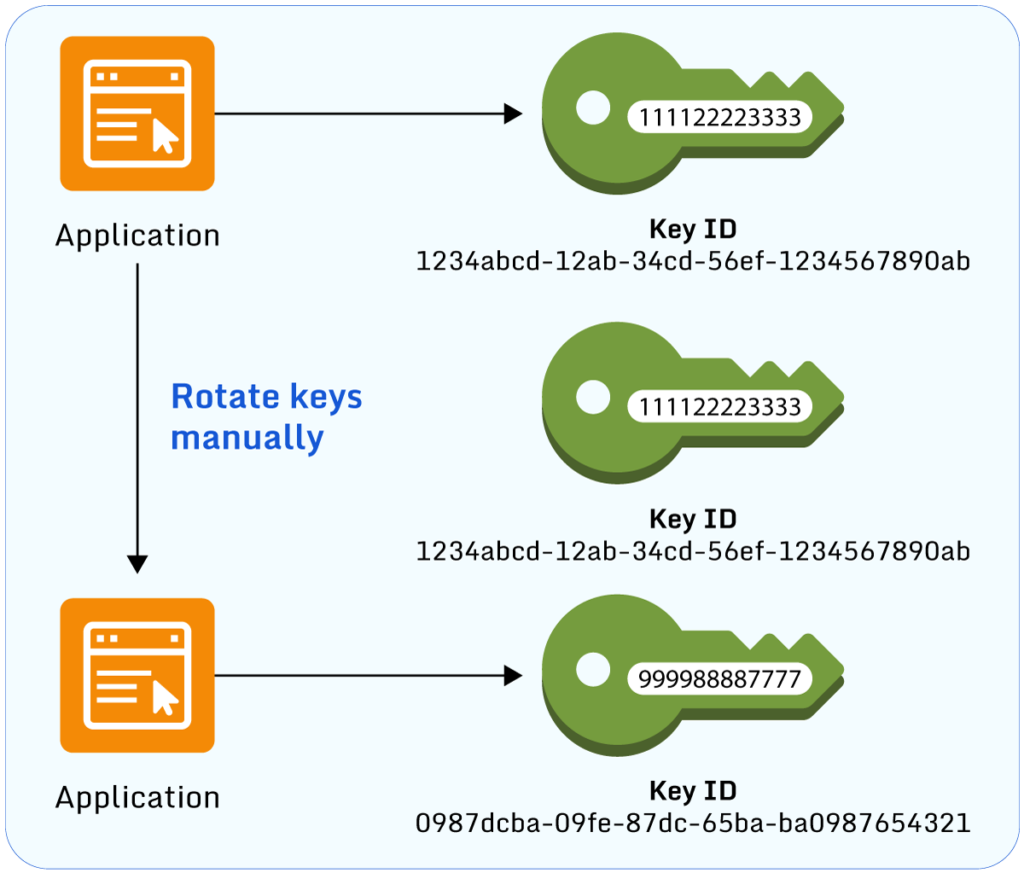
How to rotate keys with AWS KMS Paladin Cloud
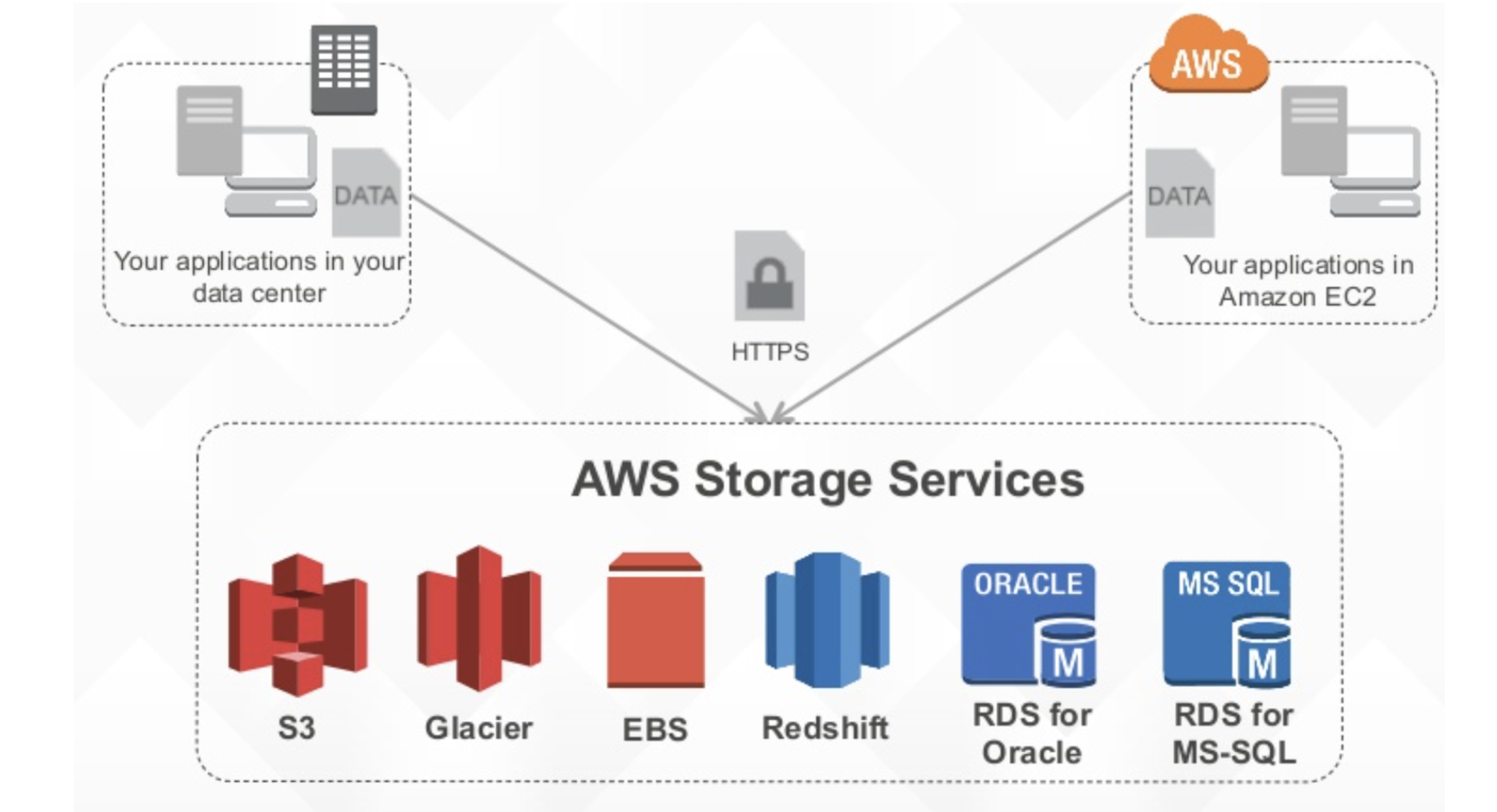
Using ServerSide Encrypt Data AWS KMS to Integrate With Mule4 AWSS3
We Assume That The Supported Aws.
The Following Code Examples Show You How To Use Aws Key Management Service With An Aws Software Development Kit (Sdk).
The Goal Of This Post Is To Create A Template That We Can Use To Generically Create New Kms Keys With Different Principals Who Are Allowed To Use The Key To Encrypt And Decrypt.
The First Template Creates A Simple Backup Plan.
Related Post: