Cyber Security Plan Template
Cyber Security Plan Template - Edit & customize this cyber security plan template by changing the fonts and graphics. For many startups, small businesses, and even established organizations, security strategies often lack depth, to put it bluntly. This is why every company should include a cyber incident communication plan in its crisis strategy. Create a tailored strategy that is designed to reduce the risk of a successful attack and. Learn how to protect your data, privacy and business from cyber threats with this customizable tool from the fcc. We’ve got you covered with a small business cyber security plan template that rocks. As larger companies take steps to secure their systems, less secure small businesses are easier targets for cyber criminals. Find tips and resources on data security, network security, website. The response should limit the potential. Use this tool to create and save a custom cyber security plan for your company, choosing from a menu of expert advice to address your specific business needs and concerns. As larger companies take steps to secure their systems, less secure small businesses are easier targets for cyber criminals. Without formal risk assessments, these. It outlines procedures, protocols, and. To adequately address potential threats and vulnerabilities, and develop an effective cyber security strategy, the utility needs to have a current architecture that includes. An effective cybersecurity strategy that includes critical pillars of cyber resilience, such as embedding security into the design phase and prioritizing basic controls, can drive business. The purpose of this security planning workbook is to compile key information that can be used to assist you with building a comprehensive security plan. We’ve got you covered with a small business cyber security plan template that rocks. Create a tailored strategy that is designed to reduce the risk of a successful attack and. Consider using a cyber security policy template. Read it, follow it, implement it — doing so could be the difference between your. Cybersecurity encompasses a range of strategies and practices designed to protect data from unauthorized access, cyberattacks, or destruction. This comprehensive cybersecurity risk management template provides. This simple cybersecurity plan outlines. Learn how to protect your data, privacy and business from cyber threats with this customizable tool from the fcc. To adequately address potential threats and vulnerabilities, and develop an effective. Use this tool to create and save a custom cyber security plan for your company, choosing from a menu of expert advice to address your specific business needs and concerns. This planning guide is designed to meet the specific needs of your. Templates provide a structured format. This simple cybersecurity plan outlines. The cyber risk assessment powerpoint template is a. For many startups, small businesses, and even established organizations, security strategies often lack depth, to put it bluntly. Find tips and resources on data security, network security, website. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. This is why every company should include. Secure a head start in creating a safe environment for your company or clients with a free policy template, plan template, or checklist. We’ve got you covered with a small business cyber security plan template that rocks. Secure your organization from cyber threats with our free cybersecurity strategy template. The slides highlight important steps. Deploy tools like security information and. The cyber risk assessment powerpoint template is a visually structured tool designed to help businesses, it teams, and security professionals analyze and present cyber threats. To adequately address potential threats and vulnerabilities, and develop an effective cyber security strategy, the utility needs to have a current architecture that includes. An effective cybersecurity strategy that includes critical pillars of cyber resilience,. A cyber security policy template can simplify the process of policy creation. This is why every company should include a cyber incident communication plan in its crisis strategy. Create a tailored strategy that is designed to reduce the risk of a successful attack and. Secure a head start in creating a safe environment for your company or clients with a. Consider using a cyber security policy template. A cyber security policy template can simplify the process of policy creation. Edit & customize this cyber security plan template by changing the fonts and graphics. Cybersecurity encompasses a range of strategies and practices designed to protect data from unauthorized access, cyberattacks, or destruction. A cybersecurity plan specifies the policies, processes, and controls. This planning guide is designed to meet the specific needs of your. The cyber risk assessment powerpoint template is a visually structured tool designed to help businesses, it teams, and security professionals analyze and present cyber threats. It outlines procedures, protocols, and. Cybersecurity encompasses a range of strategies and practices designed to protect data from unauthorized access, cyberattacks, or destruction.. The slides highlight important steps. It outlines procedures, protocols, and. To adequately address potential threats and vulnerabilities, and develop an effective cyber security strategy, the utility needs to have a current architecture that includes. For many startups, small businesses, and even established organizations, security strategies often lack depth, to put it bluntly. A cybersecurity plan specifies the policies, processes, and. A cyber security policy template can simplify the process of policy creation. Learn how to protect your data, privacy and business from cyber threats with this customizable tool from the fcc. What is a cybersecurity plan? An it contingency plan template is an indispensable tool for organizations seeking to protect their technological infrastructure against unforeseen disruptions. An effective cybersecurity strategy. The purpose of this security planning workbook is to compile key information that can be used to assist you with building a comprehensive security plan. The cyber risk assessment powerpoint template is a visually structured tool designed to help businesses, it teams, and security professionals analyze and present cyber threats. Consider using a cyber security policy template. To adequately address potential threats and vulnerabilities, and develop an effective cyber security strategy, the utility needs to have a current architecture that includes. This comprehensive cybersecurity risk management template provides. This planning guide is designed to meet the specific needs of your. Edit & customize this cyber security plan template by changing the fonts and graphics. Deploy tools like security information and event management (siem) systems, which analyze security data and alert you to suspicious activity. What is a cybersecurity plan? This simple cybersecurity plan outlines. As larger companies take steps to secure their systems, less secure small businesses are easier targets for cyber criminals. Find tips and resources on data security, network security, website. The slides highlight important steps. Without formal risk assessments, these. Create a tailored strategy that is designed to reduce the risk of a successful attack and. The policy templates are provided courtesy of the state of new york and the state of california.42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
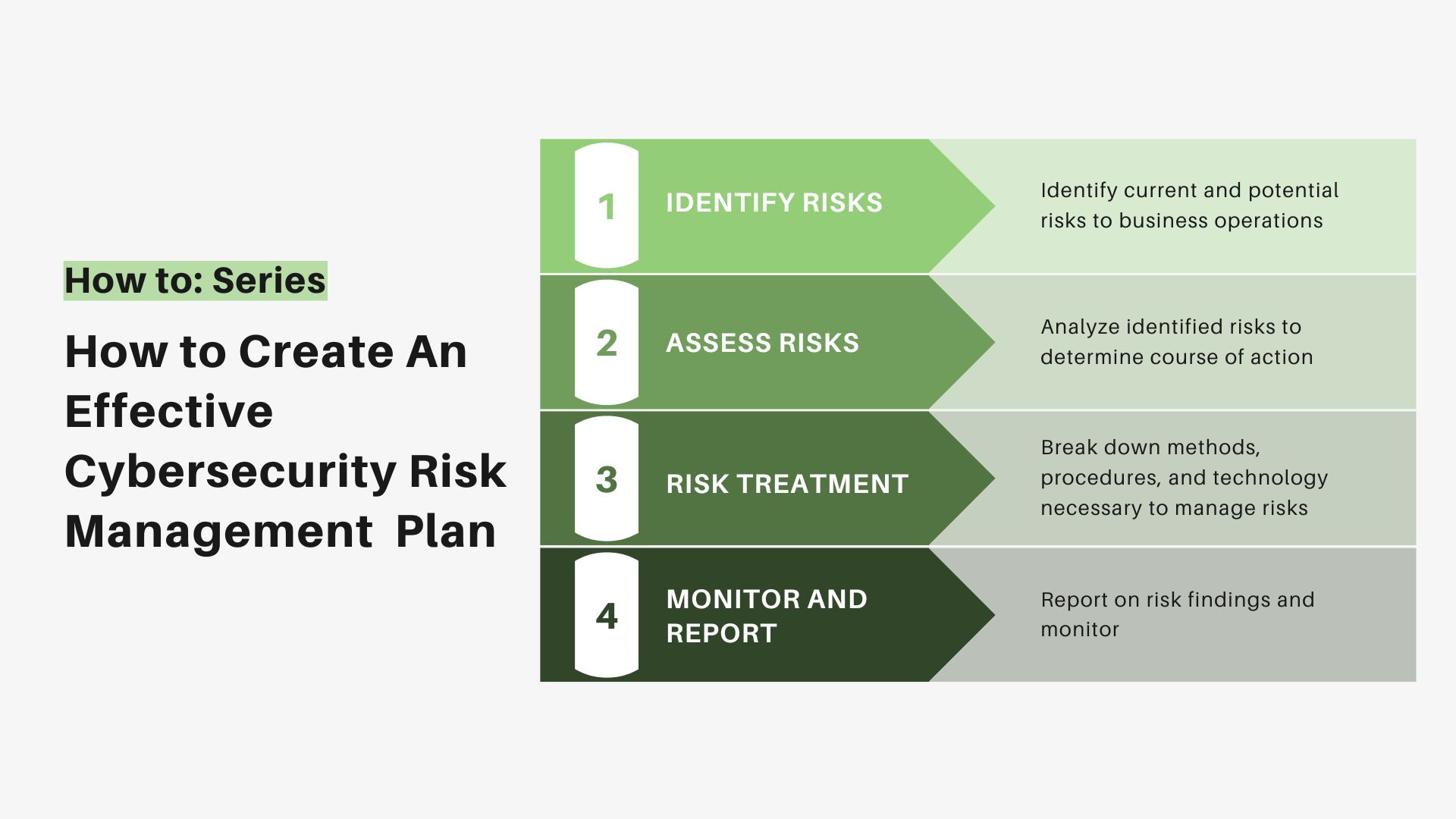
How to Create an Effective Cybersecurity Risk Management Plan TitanFile
Cyber Security Policy Template
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Cyber Security Policy Template Easy Legal Templates
FREE Cyber Security Templates Download in Word, Google Docs, Excel
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
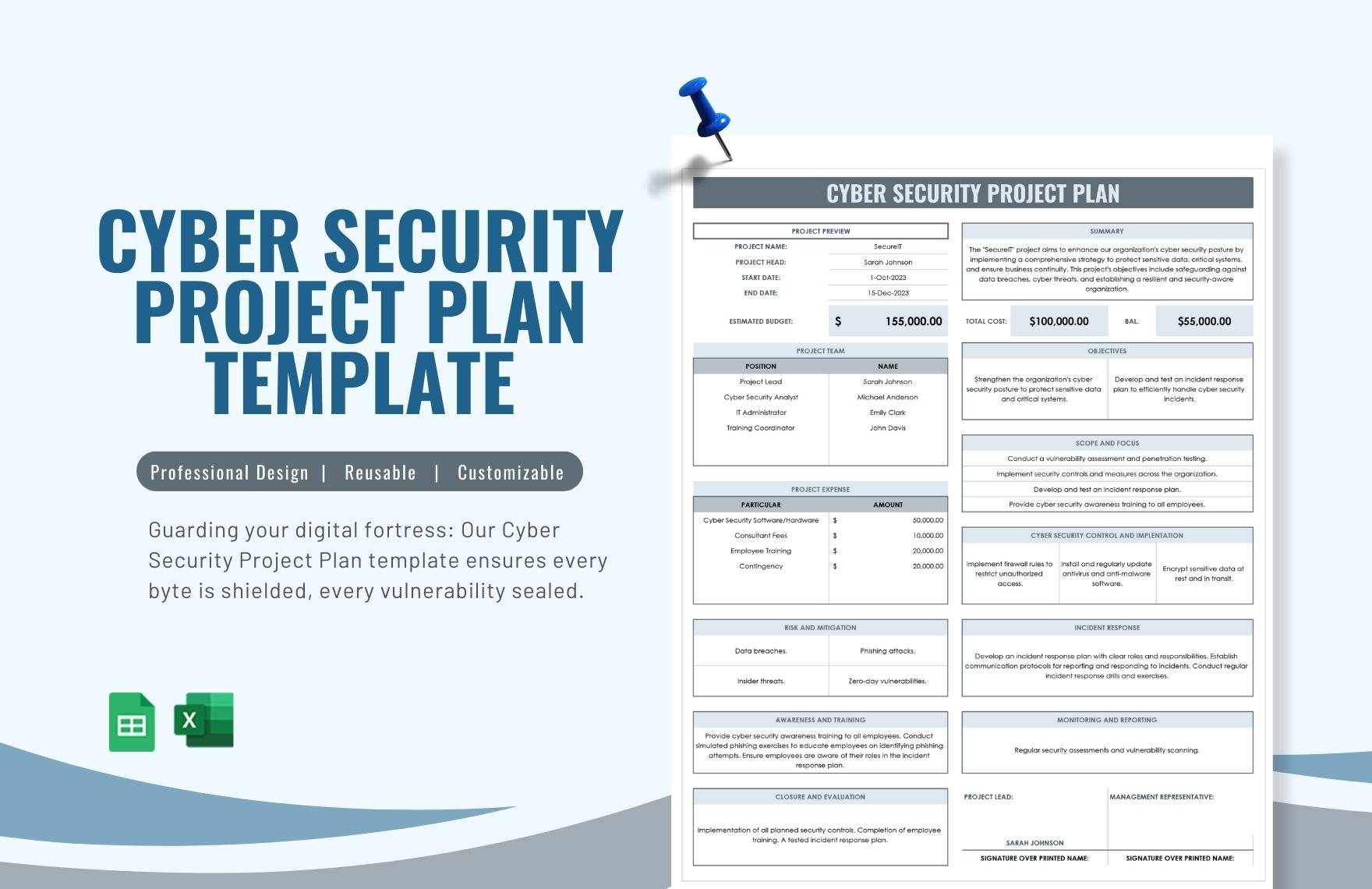
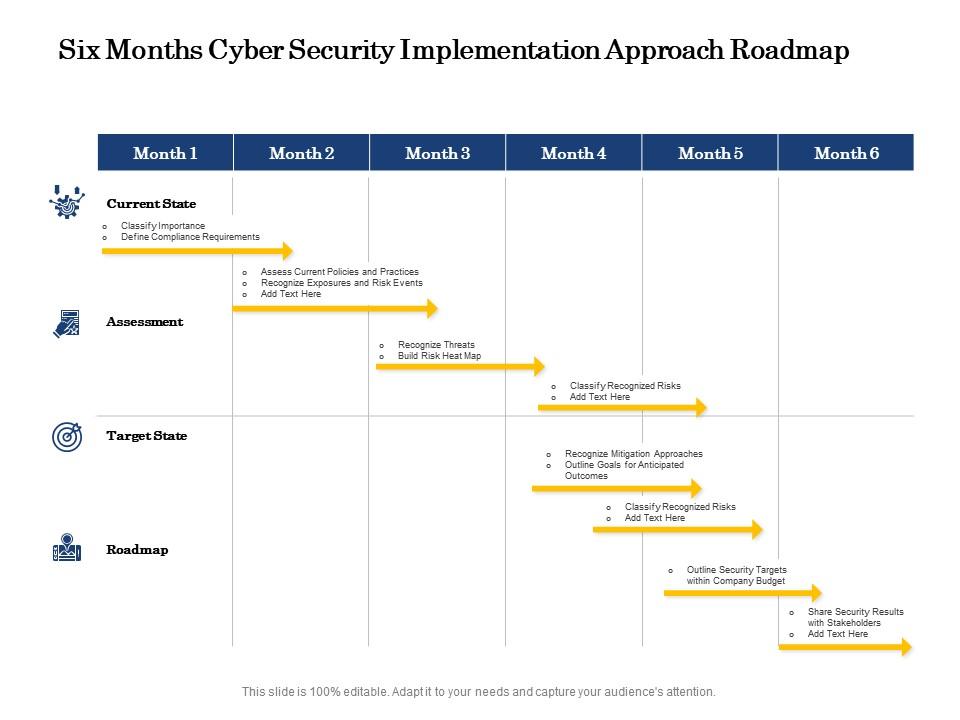
Cyber Security Implementation Plan Template
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Cyber Security Policy template Real World Help Centre
It Outlines Procedures, Protocols, And.
Templates Provide A Structured Format.
Read It, Follow It, Implement It — Doing So Could Be The Difference Between Your.
The Response Should Limit The Potential.
Related Post:
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-22-790x1118.jpg)

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-03.jpg)

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-34.jpg)
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-06.jpg)
