Information Technology Policy Templates
Information Technology Policy Templates - Why use a policy and procedure manual? Download sample information technology policy procedure template, designed to better your policies while simplifying it policy framework documentation. These downloadable, customizable it policy, procedure, and documentation templates should be a part of every company’s operations manual. Sans has developed a set of information security policy templates. Below are the essential elements your policy template should include: If you have any kind of organization, then you might have to develop your own policies regarding how the organization operates. Look no further than our comprehensive collection of it policies. Are you looking to establish guidelines and regulations for your organization's information technology infrastructure? Our list includes policy templates. Standards a standard is set of prescribed practices or. This information technology (it) policy and procedure manual is for the small to medium sized business owner and their employees. Download sample information technology policy procedure template, designed to better your policies while simplifying it policy framework documentation. The following templates are available as a guideline for agencies to develop their it security policies. Learn how to write an information security policy, and download two templates on cybersecurity and network security perimeter policies to get started. Standards a standard is set of prescribed practices or. Why use a policy and procedure manual? Processes and relationships that direct. Due to the rise of the bring your own device movement, the lines have blurred between. Your it management should have all these policies and procedures to protect all of your company electronic information and critical data. Sans has developed a set of information security policy templates. These downloadable, customizable it policy, procedure, and documentation templates should be a part of every company’s operations manual. Effective it security policy could be a model of the organization’s culture, during which rules and procedures are driven from its employees’ approach to their info and work. This document provides a template for an information technology (it) policy and procedures manual. This information technology (it) policy and procedure manual is for the small to medium sized business owner and their employees. This document provides a template for an information technology (it) policy and procedures manual for small to medium sized businesses. If you have any kind of organization, then you might have to develop your own policies regarding how the organization. Download sample information technology policy procedure template, designed to better your policies while simplifying it policy framework documentation. Learn how to write an information security policy, and download two templates on cybersecurity and network security perimeter policies to get started. Look no further than our comprehensive collection of it policies. You can customize these if you wish, for example, by. Effective it security policy could be a model of the organization’s culture, during which rules and procedures are driven from its employees’ approach to their info and work. Sans has developed a set of information security policy templates. You can customize these if you wish, for example, by adding or removing topics. Are you looking to establish guidelines and regulations. Due to the rise of the bring your own device movement, the lines have blurred between. Learn how to write an information security policy, and download two templates on cybersecurity and network security perimeter policies to get started. Are you looking to establish guidelines and regulations for your organization's information technology infrastructure? Why use a policy and procedure manual? It. These are free to use and fully customizable to your company's it security practices. Your it management should have all these policies and procedures to protect all of your company electronic information and critical data. Effective it security policy could be a model of the organization’s culture, during which rules and procedures are driven from its employees’ approach to their. Vita security baseline configurations (hardening standards) business impact. Our list includes policy templates. This document provides a template for an information technology (it) policy and procedures manual for small to medium sized businesses. The following templates are available as a guideline for agencies to develop their it security policies. It includes sample policies and procedures on. Establish clear responsibilities for everyone involved in managing and protecting information, from the. Look no further than our comprehensive collection of it policies. Are you looking to establish guidelines and regulations for your organization's information technology infrastructure? If you have any kind of organization, then you might have to develop your own policies regarding how the organization operates. Your it. For example, you would need to. Vita security baseline configurations (hardening standards) business impact. It includes sample policies and procedures on. If you have any kind of organization, then you might have to develop your own policies regarding how the organization operates. Your it management should have all these policies and procedures to protect all of your company electronic information. This information technology (it) policy and procedure manual is for the small to medium sized business owner and their employees. Our list includes policy templates. The following templates are available as a guideline for agencies to develop their it security policies. Look no further than our comprehensive collection of it policies. Your it management should have all these policies and. Why use a policy and procedure manual? Processes and relationships that direct. These are free to use and fully customizable to your company's it security practices. For example, you would need to. Our list includes policy templates. Hr resources tech & work internet and mobile phone reimbursement policy. Below are the essential elements your policy template should include: Implement successful information technology governance strategies to reduce waste, enhance security, and align it initiatives with business goals. If you have any kind of organization, then you might have to develop your own policies regarding how the organization operates. It includes sample policies and procedures on. Are you looking to establish guidelines and regulations for your organization's information technology infrastructure? Learn how to write an information security policy, and download two templates on cybersecurity and network security perimeter policies to get started. This document provides a template for an information technology (it) policy and procedures manual for small to medium sized businesses. You can customize these if you wish, for example, by adding or removing topics. Vita security baseline configurations (hardening standards) business impact. Your it management should have all these policies and procedures to protect all of your company electronic information and critical data.42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Information Technology Policy Template Elegant Ict Security and Risk
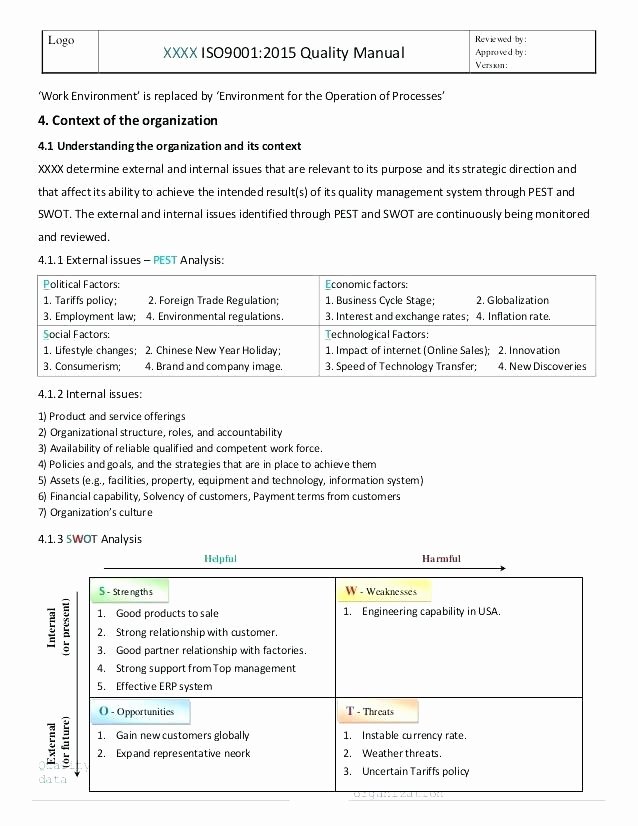
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Information Technology Policy Template
Information Technology Policies And Procedures Templates
Information Technology Policy Template
Information Technology Policy Templates
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Information Technology Policy Template
Information technology cyber security policy template in Word and Pdf
These Downloadable, Customizable It Policy, Procedure, And Documentation Templates Should Be A Part Of Every Company’s Operations Manual.
Sans Has Developed A Set Of Information Security Policy Templates.
Due To The Rise Of The Bring Your Own Device Movement, The Lines Have Blurred Between.
Information Technology Cyber Security Policy 1 Definition The Use Of The Term “Company” Is In Reverence To The Following Organization:
Related Post:
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-22.jpg)

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)



![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-08.jpg)

