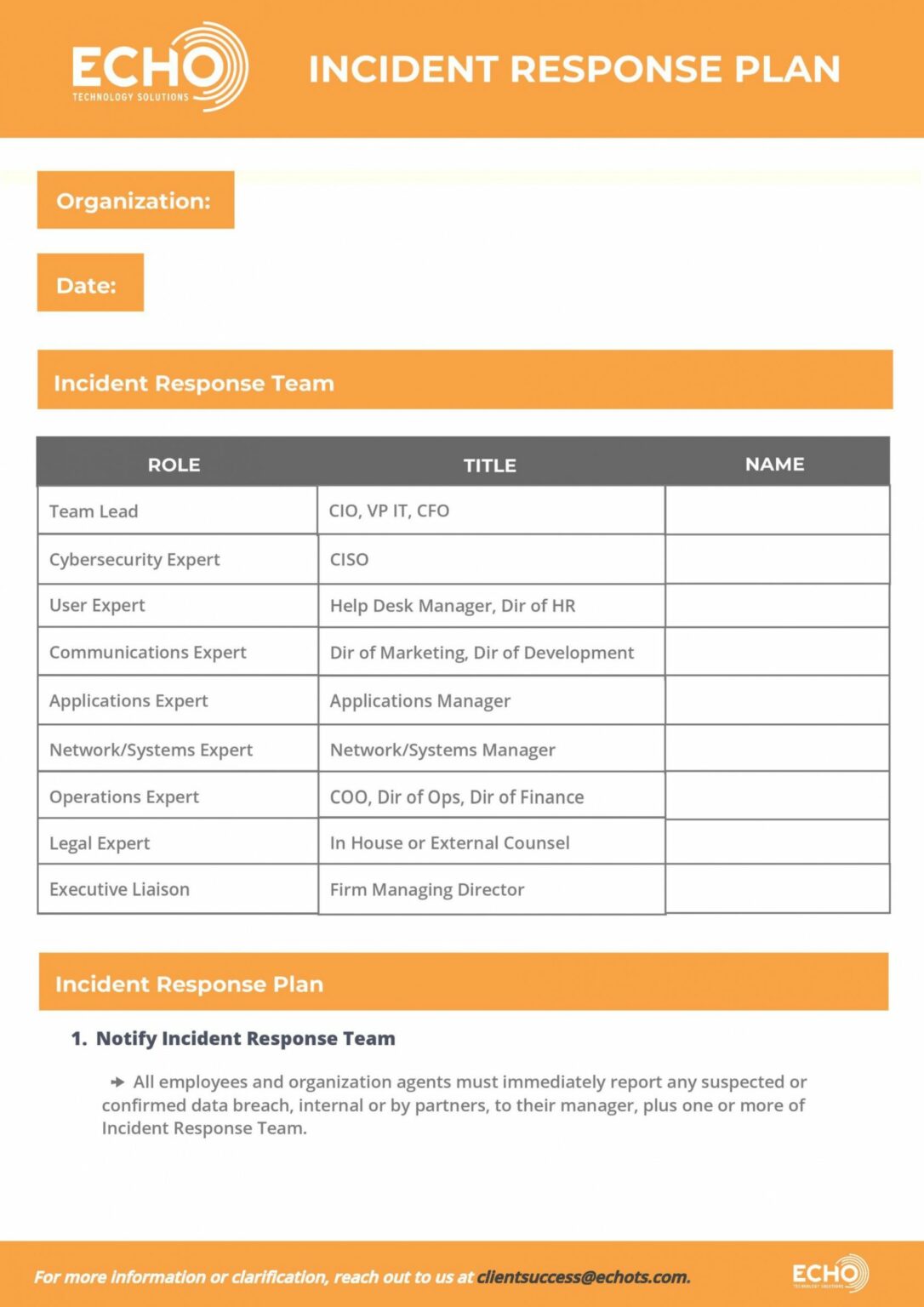
Security Incident Response Policy Template
Security Incident Response Policy Template - The templates can be used as an outline of an organizational policy, w. Security incidents should be responded to in accordance with documented incident response procedures. Our list includes policy templates. That statistic alone tells us a great deal about the importance of preparedness for a potential cyberattack, which includes a robust incident response plan. Develop an incident management plan to proactively assess potential cyber threats and outline strategies to address them. These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. This incident response policy template provides a comprehensive framework for managing cybersecurity incidents. This security incident response policy is intended to establish controls to ensure detection of security vulnerabilities and incidents, as well as quick reaction and response to security. The document provides a template for an incident response policy and plan. It includes sections on the incident response lifecycle, purpose of the policy, roles and responsibilities, and. This incident response policy template provides a comprehensive framework for managing cybersecurity incidents. The document provides a template for an incident response policy and plan. The templates can be used as an outline of an organizational policy, w. To create such a plan, it. Here’s a handy template to get you started! Companies must be ready to respond effectively to cyber incidents to restore critical business functions. The best way to be fully prepared for incidents is by having a. An incident response policy template is a document that outlines the roles and responsibilities of your incident response team, the steps and actions to take in case of a security breach, and. Our list includes policy templates. Think of it as your incident management playbook, ready to be personalized to fit your organization’s unique needs and goals. The document provides a template for an incident response policy and plan. By establishing an incident response plan, defining roles and responsibilities, and implementing security controls, organizations can effectively prepare for handling incidents. This incident response policy template provides a comprehensive framework for managing cybersecurity incidents. Security incidents should be responded to in accordance with documented incident response procedures. This. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. These are free to use and fully customizable to your company's it security practices. Security incidents should be responded to in accordance with documented incident response procedures. When building your incident response plan, it is. Security incidents should be responded to in accordance with documented incident response procedures. There are several resources that can help you develop your incident response plan. Download now to fortify your defenses against cyber threats. 5 steps to building an incident response plan. Sans has developed a set of information security policy templates. This incident response policy template provides a comprehensive framework for managing cybersecurity incidents. The response should limit the potential. Here’s a handy template to get you started! In addition to nist, there is sans incident. The best way to be fully prepared for incidents is by having a. When a cyber security incident occurs, timely and thorough action to manage the impact of the incident is a critical to an effective response process. Knowledge gained from analyzing and resolving security incidents should be. 5 steps to building an incident response plan. Companies must be ready to respond effectively to cyber incidents to restore critical business functions. Develop an. Companies must be ready to respond effectively to cyber incidents to restore critical business functions. These are free to use and fully customizable to your company's it security practices. This security incident response policy is intended to establish controls to ensure detection of security vulnerabilities and incidents, as well as quick reaction and response to security. The response should limit. 5 steps to building an incident response plan. The templates can be used as an outline of an organizational policy, w. Think of it as your incident management playbook, ready to be personalized to fit your organization’s unique needs and goals. These are free to use and fully customizable to your company's it security practices. Sans has developed a set. The best way to be fully prepared for incidents is by having a. 5 steps to building an incident response plan. Our list includes policy templates. This security incident response policy is intended to establish controls to ensure detection of security vulnerabilities and incidents, as well as quick reaction and response to security. An incident response policy template is a. There are several resources that can help you develop your incident response plan. The best way to be fully prepared for incidents is by having a. These are free to use and fully customizable to your company's it security practices. When building your incident response plan, it is much easier to start with a template, remove parts that are less. Knowledge gained from analyzing and resolving security incidents should be. Our list includes policy templates. The document provides a template for an incident response policy and plan. Secure your business today with our free incident response policy template! That statistic alone tells us a great deal about the importance of preparedness for a potential cyberattack, which includes a robust incident. That statistic alone tells us a great deal about the importance of preparedness for a potential cyberattack, which includes a robust incident response plan. An incident response policy template is a document that outlines the roles and responsibilities of your incident response team, the steps and actions to take in case of a security breach, and. 5 steps to building an incident response plan. Download now to fortify your defenses against cyber threats. Security incidents should be responded to in accordance with documented incident response procedures. In addition to nist, there is sans incident. It includes sections on the incident response lifecycle, purpose of the policy, roles and responsibilities, and. Our list includes policy templates. Knowledge gained from analyzing and resolving security incidents should be. Companies must be ready to respond effectively to cyber incidents to restore critical business functions. The templates can be used as an outline of an organizational policy, w. This security incident response policy is intended to establish controls to ensure detection of security vulnerabilities and incidents, as well as quick reaction and response to security. Sans has developed a set of information security policy templates. Here’s a handy template to get you started! These playbooks provide fceb agencies with a standard set of procedures to identify, coordinate, remediate, recover, and track successful mitigations from incidents and. Secure your business today with our free incident response policy template!Free Security Incident Response Plan Template Edit Online & Download
Free, Editable Cybersecurity Incident Response Plan Template
Incident Response Plan Template
Security Incident Response Policy Template
Free Cybersecurity Incident Response Plan Template Printable Templates
Free Incident Response Policy Template [No Email Required]
Security Incident Response Plan Template Printable Word Searches
Security Incident Response Plan Template Google Docs, Word, Apple
Free Cybersecurity Incident Response Plan Template Develop Your Plan
Printable Cybersecurity Incident Response Plan Template Echo Cyber
Think Of It As Your Incident Management Playbook, Ready To Be Personalized To Fit Your Organization’s Unique Needs And Goals.
The Response Should Limit The Potential.
Develop An Incident Management Plan To Proactively Assess Potential Cyber Threats And Outline Strategies To Address Them.
To Create Such A Plan, It.
Related Post:


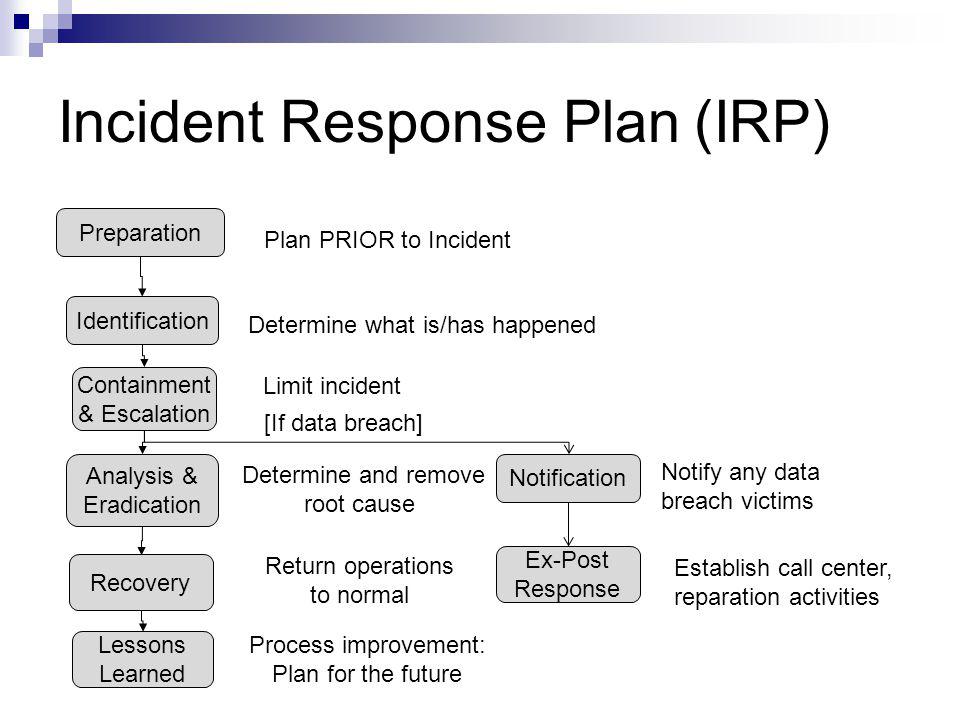


![Free Incident Response Policy Template [No Email Required]](https://adeliarisk.com/wp-content/uploads/2023/06/incident-response-policy-template-page-one.png)