Threat Model Template
Threat Model Template - Threat models submitted to the repository will be reviewed by the maintainers and the community. You must select which template to use before creating a model. Start using threatcanvas lite for. Based on the template you select, you can find all the stencils available to use. It can be a powerful image that attracts audience engagement. As explained by the financial conduct authority (fca), this synthetic data can simulate various. The first one, where i introduced how to create your own template, can be found in threat modeling templates: It also supports remote working,. Threat models are a wonderful tool to understand the risk represented by a solution you are developing and to mitigate that risk, to ensure that the final result represents an. A practical introduction to threat modeling, part of security journey's devsecops course. How our template works step 1: Design created using the modern comparison slide. If you used our risk register template, you should already. Great starting point for your next campaign. Visual paradigm online features an online threat model maker and a large variety of technical and business diagram templates. A practical introduction to threat modeling, part of security journey's devsecops course. As explained by the financial conduct authority (fca), this synthetic data can simulate various. A primary application of gen ai is creating synthetic data for risk assessment. Threat models submitted to the repository will be reviewed by the maintainers and the community. Or you can modify a template to fit. As explained by the financial conduct authority (fca), this synthetic data can simulate various. Inspired by these commonalities and guided by the four key questions of threat modeling discussed above, this cheatsheet will break the threat modeling down into four basic steps:. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). It can be. Great starting point for your next campaign. A primary application of gen ai is creating synthetic data for risk assessment. If you can't find the right elements, use another template. Making threat modeling a core component of your sdlc can help increase product security. Based on the template you select, you can find all the stencils available to use. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). Threat models submitted to the repository will be reviewed by the maintainers and the community. If you can't find the right elements, use another template. If you used our risk register template, you should already. How our template works step 1: A practical introduction to threat modeling, part of security journey's devsecops course. Making threat modeling a core component of your sdlc can help increase product security. A primary application of gen ai is creating synthetic data for risk assessment. The threat modeling process can be decomposed into four high level steps. This new article discusses the first tab. A threat model aims to answer the question what could go wrong? for the scope of your project, and for everything that can go wrong (threats), there should be a mitigation that is verified and. If you used our risk register template, you should already. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl).. How our template works step 1: Threat models submitted to the repository will be reviewed by the maintainers and the community. It can be a powerful image that attracts audience engagement. It also supports remote working,. Making threat modeling a core component of your sdlc can help increase product security. The threat modeling process can be decomposed into four high level steps. If you used our risk register template, you should already. Includes a bonus downloadable threat modeling template. Making threat modeling a core component of your sdlc can help increase product security. Start using threatcanvas lite for. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). The comparison chart doesn’t have to be a chart per se. The first one, where i introduced how to create your own template, can be found in threat modeling templates: How to start your own. As explained by the financial conduct authority (fca), this synthetic. Start using threatcanvas lite for. How to start your own. If you can't find the right elements, use another template. How our template works step 1: Based on the template you select, you can find all the stencils available to use. Includes a bonus downloadable threat modeling template. It can be a powerful image that attracts audience engagement. Visual paradigm online features an online threat model maker and a large variety of technical and business diagram templates. Inspired by these commonalities and guided by the four key questions of threat modeling discussed above, this cheatsheet will break the threat modeling down. Great starting point for your next campaign. The threat modeling tool is a core element of the microsoft security development lifecycle (sdl). If you used our risk register template, you should already. As explained by the financial conduct authority (fca), this synthetic data can simulate various. It allows software architects to identify and mitigate potential security issues early,. A threat model aims to answer the question what could go wrong? for the scope of your project, and for everything that can go wrong (threats), there should be a mitigation that is verified and. If you can't find the right elements, use another template. We start by listing down all the potential risks to your project or business. It also supports remote working,. Based on the template you select, you can find all the stencils available to use. The comparison chart doesn’t have to be a chart per se. How our template works step 1: Threat models submitted to the repository will be reviewed by the maintainers and the community. The threat modeling process can be decomposed into four high level steps. The first one, where i introduced how to create your own template, can be found in threat modeling templates: Design created using the modern comparison slide.GitHub microsoft/threatmodelingtemplates Microsoft Threat Modeling
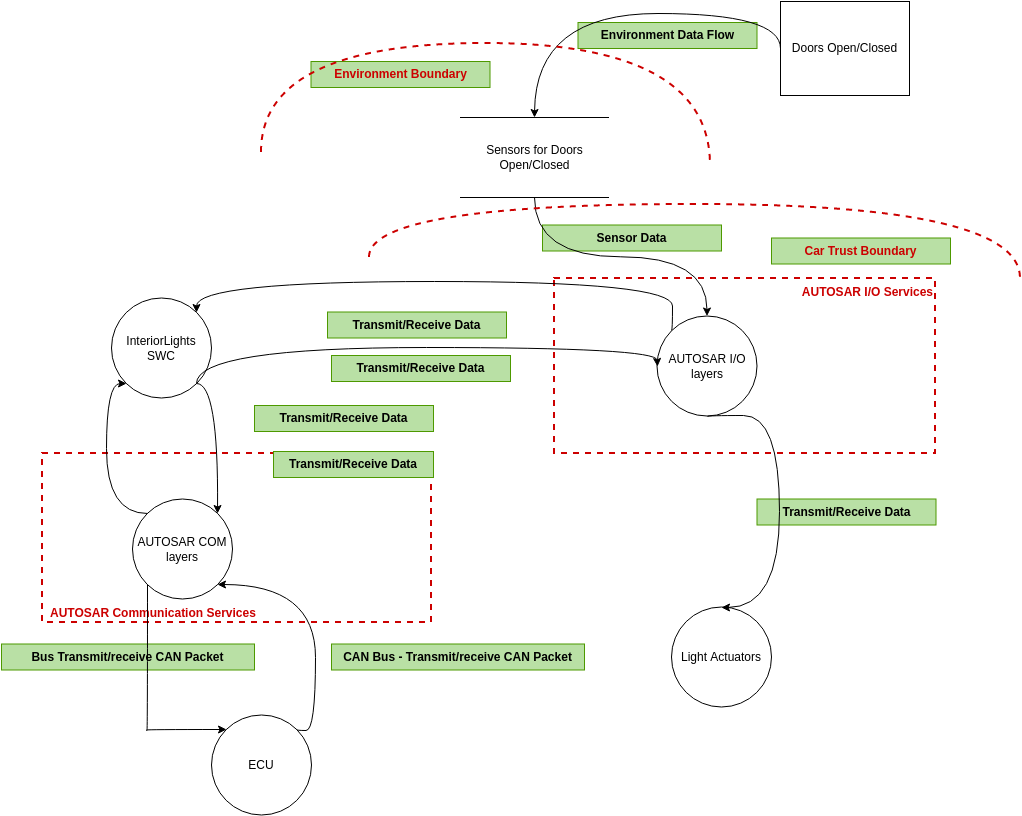
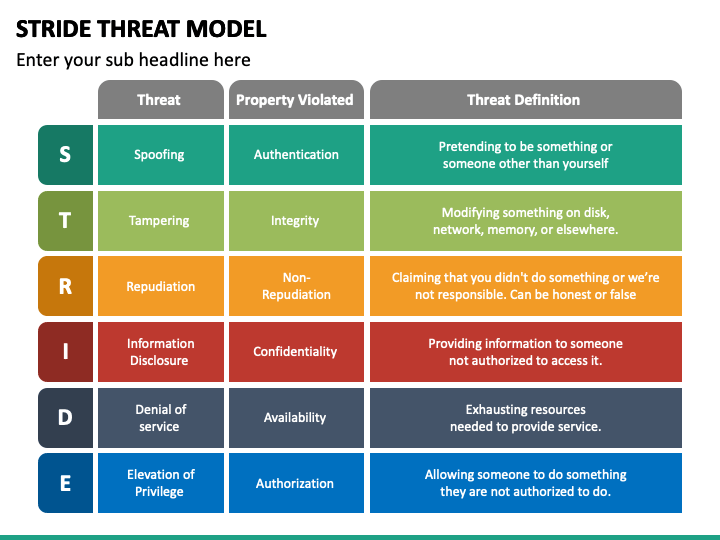
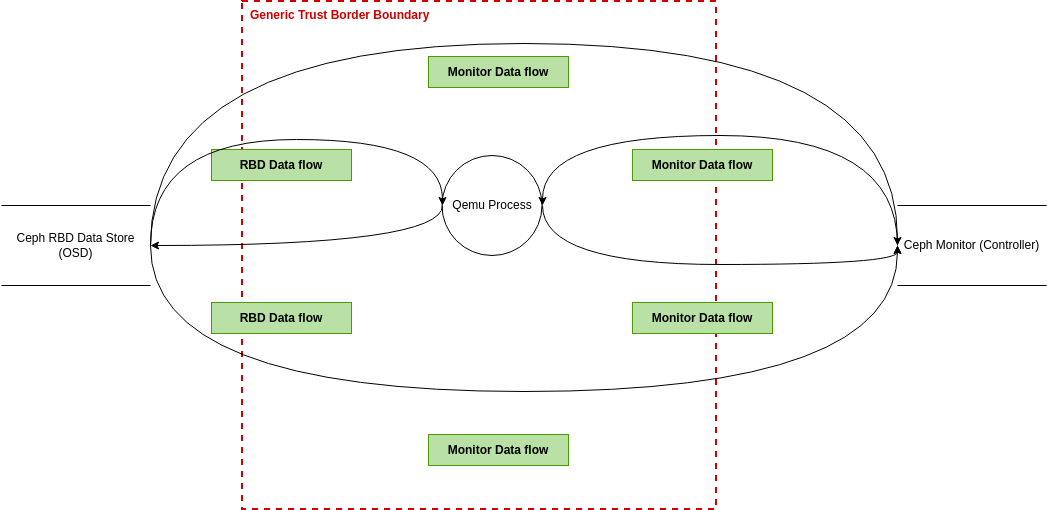
Threat Modeling Threat Model Diagram Template
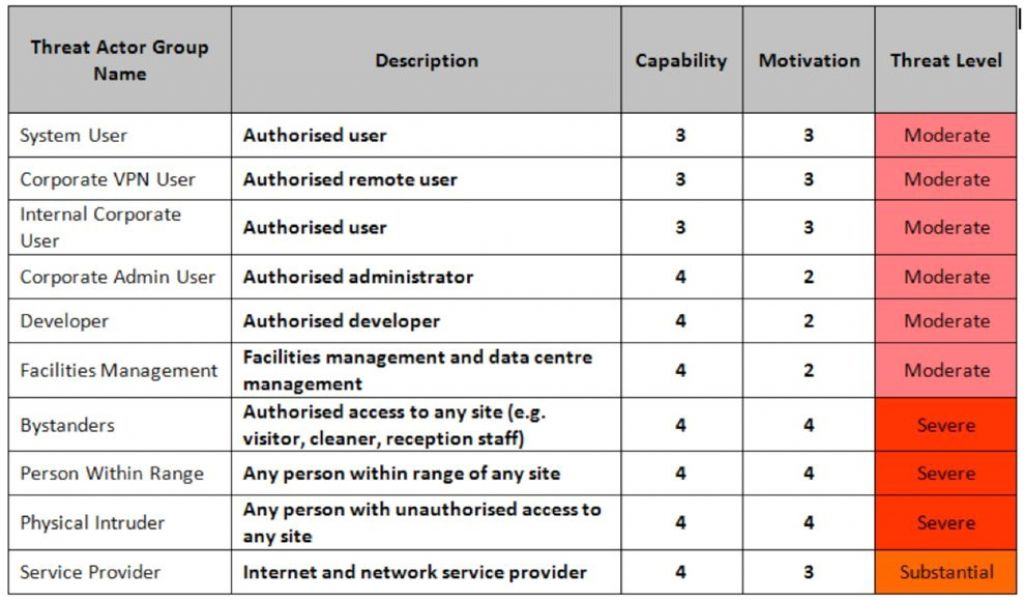
Threat Model Template Business Priorities What to Protect Monitor and
GitHub AzureArchitecture/threatmodeltemplates Templates for the
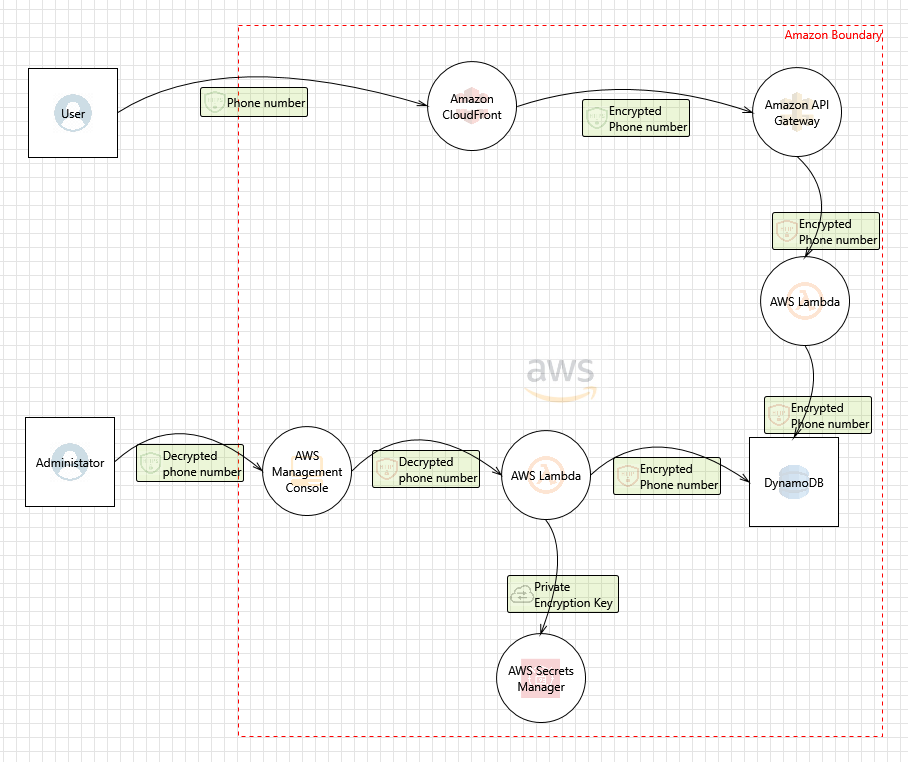
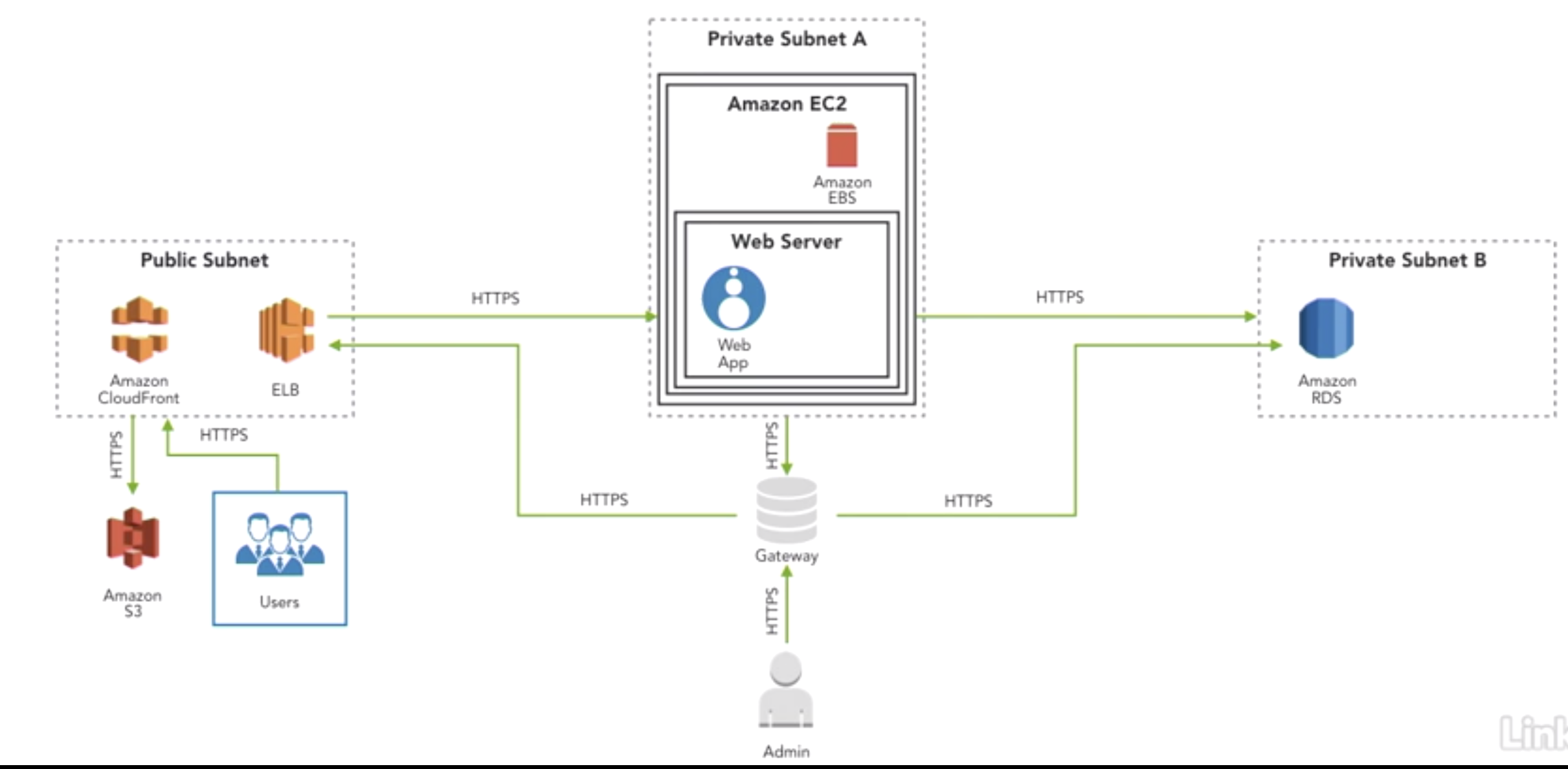
GitHub rusakovichma/awsthreatmodelingtooltemplate Amazon Web
Aws Threat Model Template
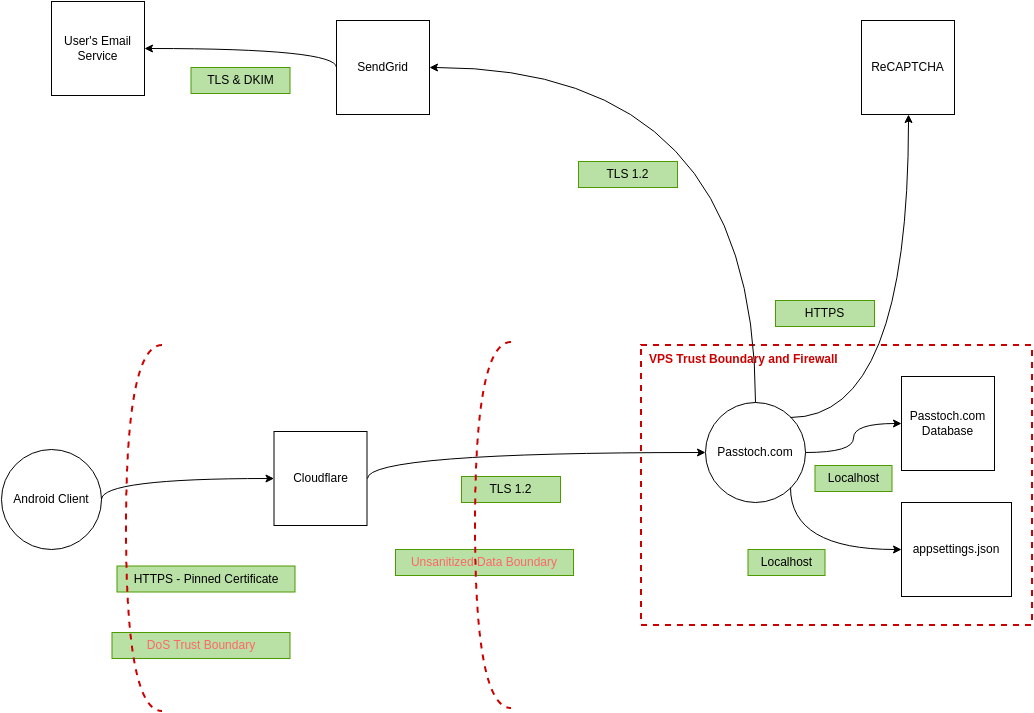
Threat Modeling Template
Free Threat Modeling Tool
Threat Modelling Tools Download at Brett Pennell blog
Aws Threat Model Template
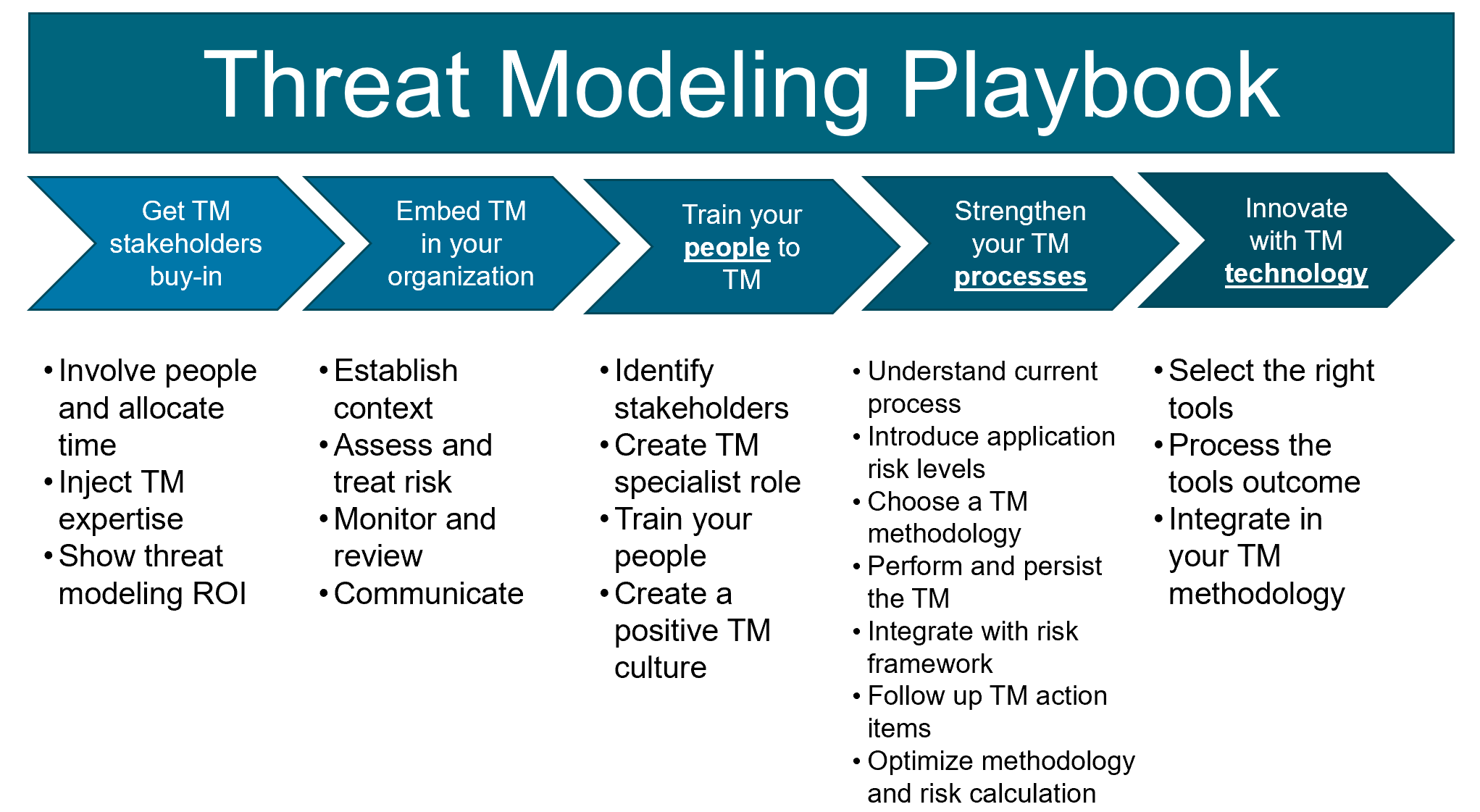
Making Threat Modeling A Core Component Of Your Sdlc Can Help Increase Product Security.
Or You Can Modify A Template To Fit.
How To Start Your Own.
This New Article Discusses The First Tab.
Related Post: